Introduction to AWS WAF:
In recent years, security has become a top priority for most companies. Thankfully, there are numerous services available to help you enhance the security of your AWS environment.
One such service is AWS WAF (Web Application Firewall), a firewall that provides protection to your web application server against a range of Internet threats.
With the prevalence of web application attacks, including cross-site scripting (XSS), SQL injection, and cookie poisoning, among others, the need for a reliable security tool to safeguard your web applications is crucial.
Deploying a WAF solution provides an effective defense mechanism against malicious traffic, helping to prevent a variety of attacks that can compromise your systems and lead to data exfiltration.
By leveraging AWS WAF, you can ensure the security and availability of your web applications, allowing you to focus on running your business with confidence.
Why is WAF security is important ?
As more and more enterprises offer products and services online, such as online banking, social media platforms, and mobile application development, a Web Application Firewall (WAF) becomes increasingly crucial in preventing data leakage.
Backend databases, which can be accessed through web applications, store a range of sensitive data such as credit card information and customer records.
These applications are frequently targeted by attackers to gain unauthorized access to sensitive data. Therefore, deploying a WAF is essential for protecting against such attacks, as it acts as a shield, blocking malicious traffic and preventing data breaches.
For enterprises that rely on web applications to handle sensitive data, a WAF solution is a crucial security measure that can help mitigate the risk of costly data leaks and reputational damage.
WAF v/s Firewall v/s Shield :
AWS offers several security services, including AWS WAF, AWS Firewall Manager, and AWS Shield, which provide different types of protection to your AWS environment.
AWS WAF is a powerful security tool designed to safeguard web applications from various types of web exploits and attacks that are commonly encountered on the internet. These include but are not limited to cross-site scripting (XSS), SQL injection, and HTTP flooding. It operates at the application layer of the OSI model and provides granular control over web traffic to your applications.
AWS Firewall Manager, on the other hand, is a service that makes it easier to deploy and manage network firewalls across multiple AWS accounts and resources. It centralizes firewall management and allows you to create and enforce firewall rules and policies across your entire AWS infrastructure.
AWS Shield is a fully managed service that provides protection against Distributed Denial of Service (DDoS) attacks for your web applications and resources. It is specifically designed to help prevent DDoS attacks from disrupting your online services, allowing you to maintain the availability of your applications and keep your customers’ data secure.AWS Shield provides protection against several types of DDoS attacks, including volumetric attacks, protocol attacks, and application layer attacks.
In summary, AWS WAF, AWS Firewall Manager, and AWS Shield provide different types of protection to your AWS environment. AWS WAF is designed to protect web applications from application-layer attacks, while AWS Firewall Manager helps manage network firewalls across multiple AWS accounts and resources. AWS Shield is designed to protect web applications and resources from DDoS attacks. All three services work together to provide comprehensive protection for your AWS infrastructure.
What is AWS WAF (Web Application Firewall) ?
The AWS Web Application Firewall (WAF) serves as a security solution that safeguards your applications from web-based attacks. By scrutinizing and regulating suspicious bot traffic, it thwarts standard attack patterns like Cross-site scripting or SQL Injection. Additionally, the tool empowers you to observe the HTTP and HTTPS requests that reach an Application Load Balancer, Amazon CloudFront, or an Amazon API Gateway API.
- By utilizing the IP address from which the request originated, Amazon WAF empowers you to regulate your content.
- The workings of Amazon WAF rely on three key elements – Access Control Lists (ACLs), Rules, and Rule Groups.
- Amazon WAF oversees the Web ACL Capacity Units (WCUs) that pertain to rules, rule groups, and web ACLs.
- Amazon WAF comes with a comprehensive API that enables you to automate the process of creating, deploying, and maintaining security rules.
Configuring AWS WAF:
By using AWS Web Application Firewall (WAF), web applications can be shielded from malicious attacks. The following outlines the way in which AWS WAF operates.
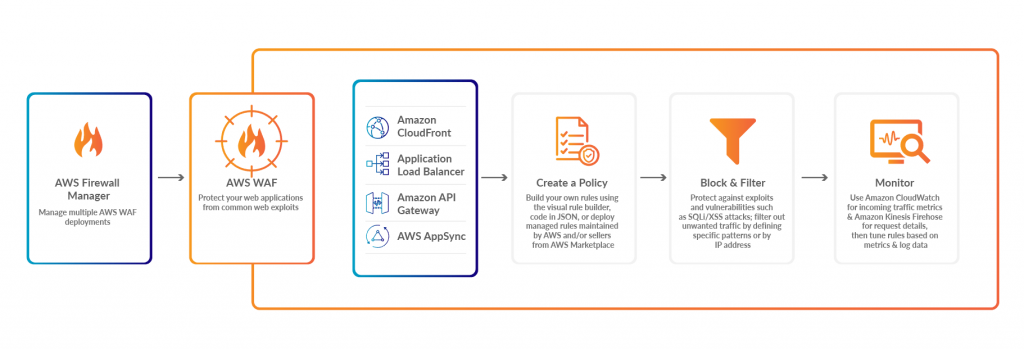
AWS Firewall Manage: AWS Firewall Manager is a service that allows you to centrally configure and manage firewalls across multiple accounts and resources within an AWS organization. With Firewall Manager, you can create firewall rules, audit and remediate non-compliant resources, and protect your resources against attacks.
AWS WAF: AWS WAF works with Amazon CloudFront and Application Load Balancer to provide protection for web applications. When a user requests content from your application, the request is first sent to CloudFront or Application Load Balancer, which checks if the request matches any of the rules defined in your AWS WAF policy. If the request matches a rule, it is blocked or allowed based on the rule’s action.
To establish a policy in AWS, there are several options available. You can create your own rules using the visual rule builder, write code in JSON format, or deploy managed rules that are maintained by AWS or third-party vendors from the AWS Marketplace.
Block Filter: Block filters are a security measure that provides protection against attacks exploiting vulnerabilities and exploits.
Test and Monitor: Once you have configured your AWS WAF rules, it is important to test them to ensure that they are working correctly. You can do this by using the AWS WAF console to simulate various types of web requests and verify that the appropriate rules are being applied. You should also set up logging and monitoring for your AWS WAF deployment to track traffic patterns and identify potential threats.
Getting Started With AWS WAF
AWS WAF is capable of monitoring all incoming and outgoing web requests that are transmitted to Amazon API Gateway, Application Load Balancer, and Amazon CloudFront. To get started with WAF and create a web ACL, you can follow these simple steps.
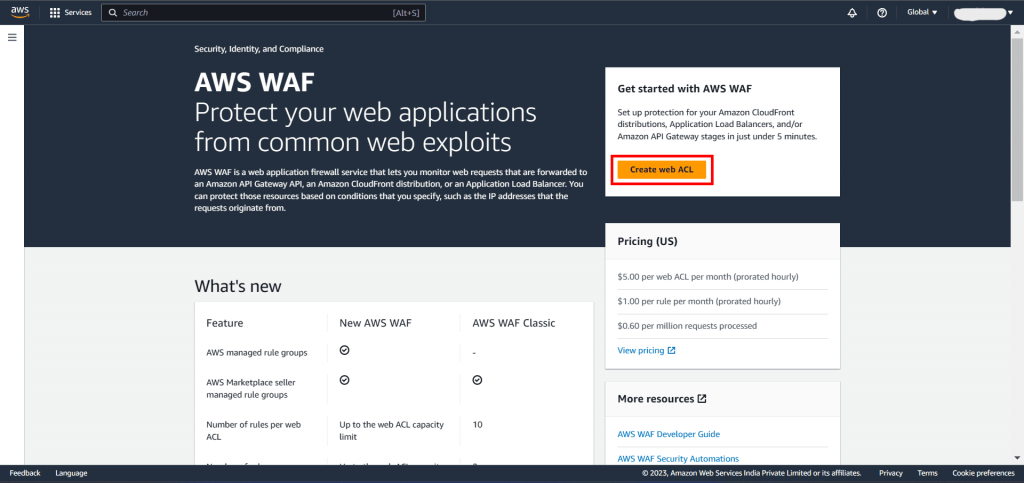
Step 1: Create web ACL: To get started, register for an AWS account, then navigate to the AWS Console and search for Web Application Firewall. This will take you to the WAF homepage, where you can select the option to create a new Web ACL.
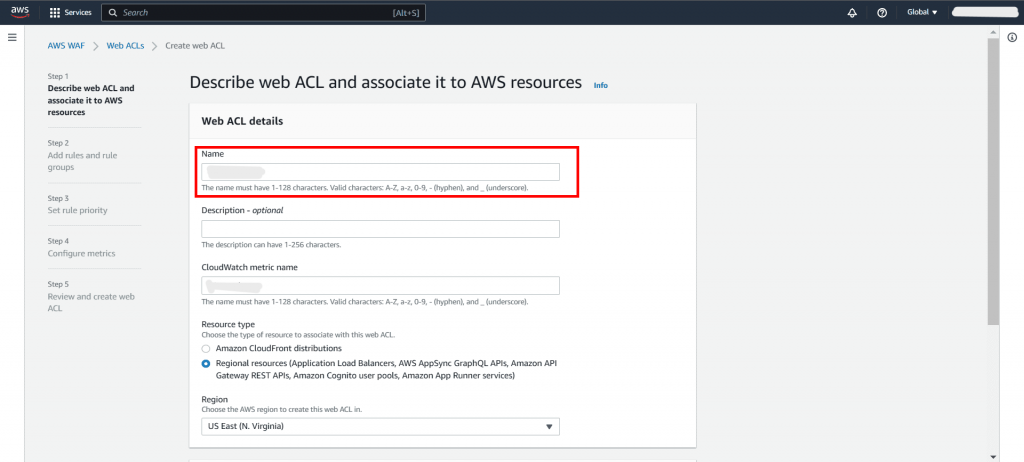
Step 2: Give a Name: Enter a name to identify the Web ACL, and if desired, add an optional description. Click “Next” once you have completed this step.
Step 3: Add an AWS Managed Rules rule group: The next step involves adding rule groups and rules to your Web ACL. To do this, click on “Add managed rule groups” and you will be directed to a new page where you can manage the rule groups as shown in Snapshot 2.
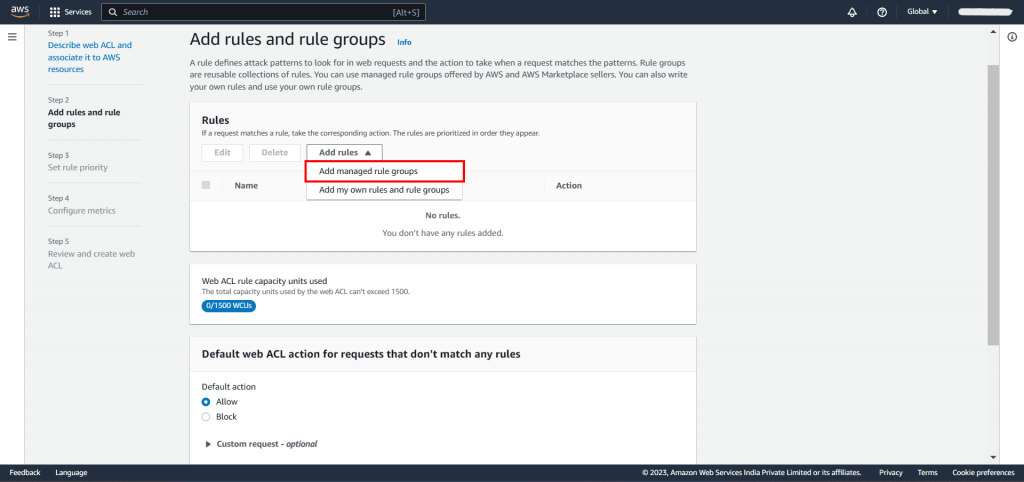
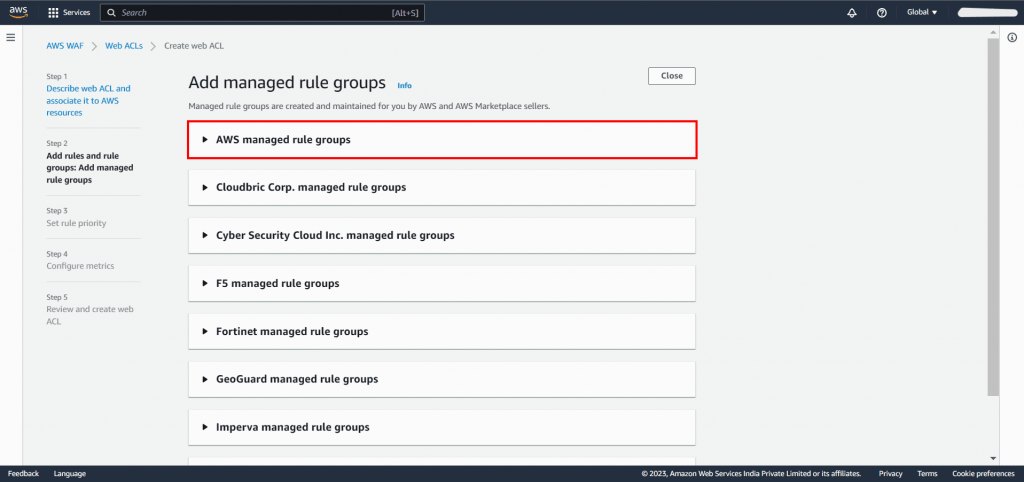
With AWS Managed Rules, you have access to a range of managed rule groups, most of which are available free of charge for Amazon WAF users. Once you’ve added a managed rule group, simply select the option to save the rule.
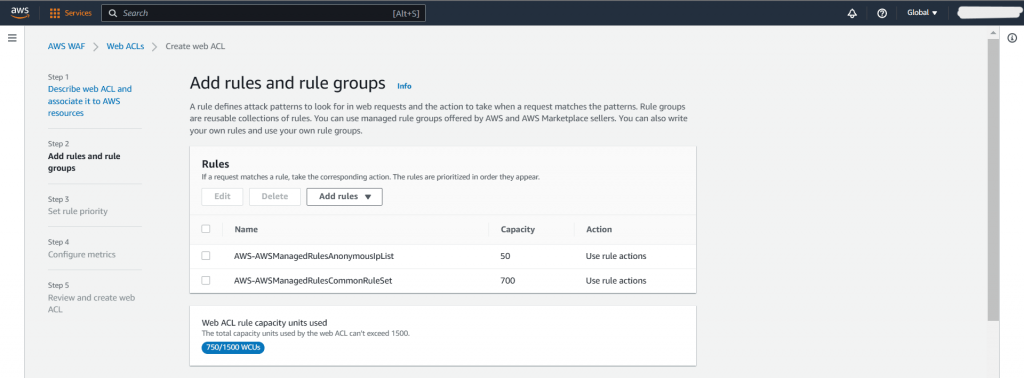
We will use the rules we create to specify the patterns we want to permit or deny. Specifically, we will be adding only two rules.
Regular rule: This rule safeguards the application against SQL injection attacks by verifying whether the URI path includes any SQL injection attempts.
Rate-based rule: After a set threshold of requests made within a specific time frame is surpassed, this rule prohibits further requests originating from the same IP address.
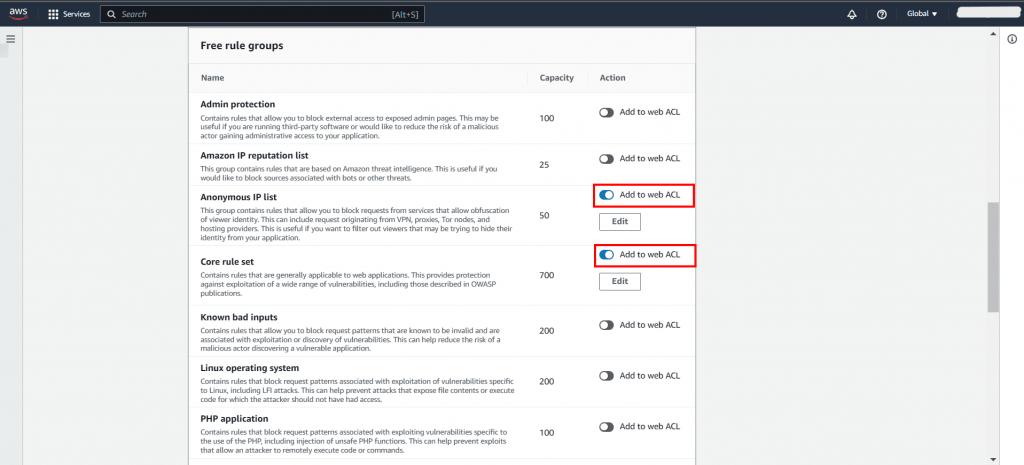
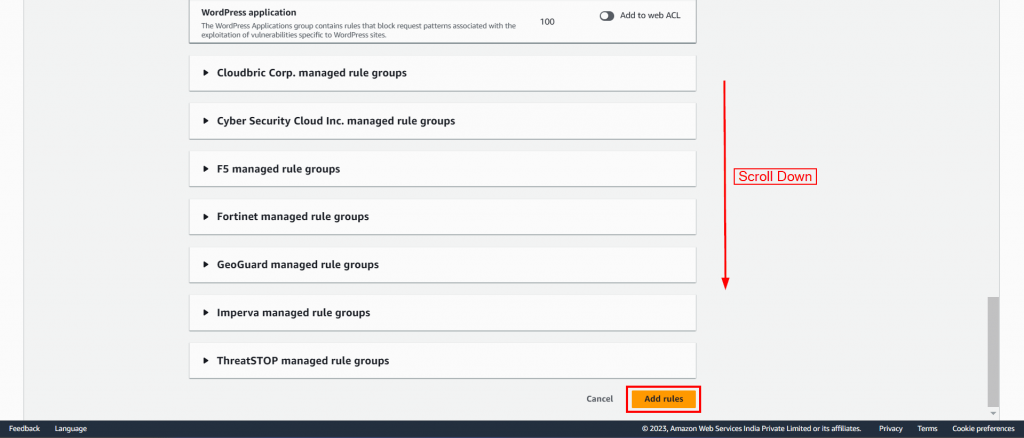
Once you have added the rules, review them and then click on “Next.”
Step 4: Configure Cloudwatch Metrics:
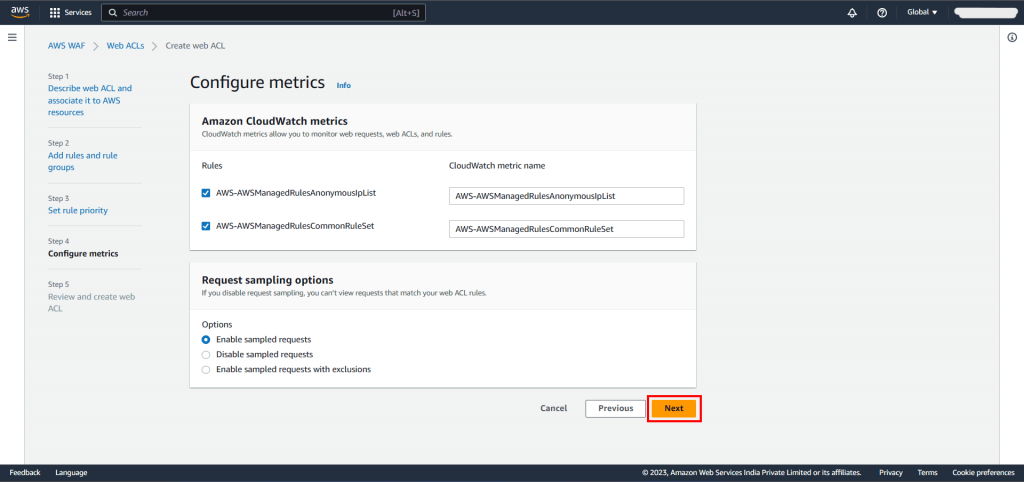
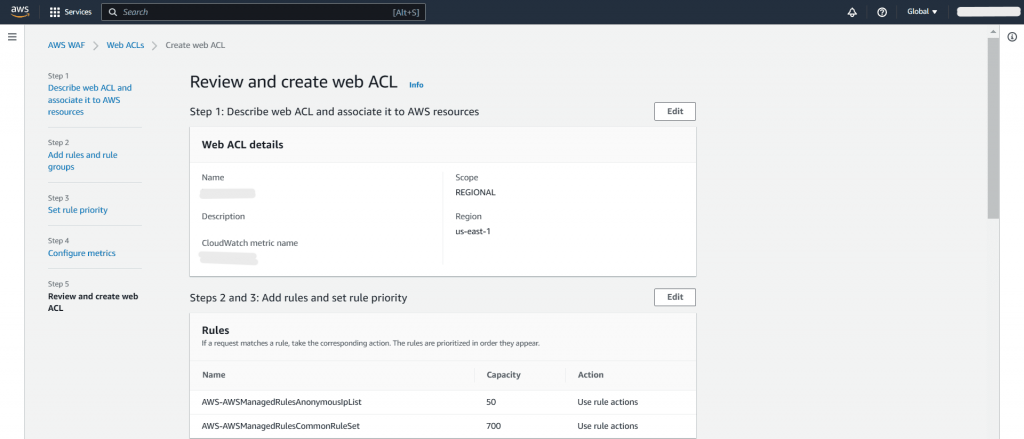
Step 5: Review Web ACL Configuration: In the last step, verify all of the rules and managed groups, and then select Create Web ACL.
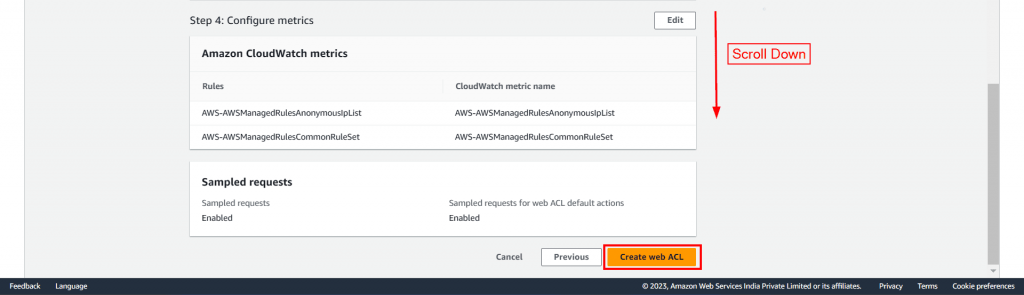
Lastly, a message will appear stating, “You have successfully created web ACL: ACL-name.”
Overall, AWS WAF is a powerful tool for protecting web applications from cyber attacks and should be considered by any organization that wants to secure their web traffic.
Best practices for using AWS WAF:
- Regularly update your rules: Keep your rules up to date to protect against the latest threats and attacks. AWS Managed Rules automatically updates to protect against the latest threats, so consider enabling this feature.
- Use rate-based rules to protect against DDoS attacks: Rate-based rules allow you to protect against DDoS attacks by limiting the number of requests that can be made in a certain time period.
- Use the AWS WAF Security Automations solution: AWS offers a pre-built solution that includes AWS WAF, AWS Shield, and Amazon CloudFront to provide protection against common web exploits and threats.
- Use logging and metrics: Enable logging and metrics to track traffic patterns, identify potential threats, and monitor your WAF’s performance.
- Test your rules: Regularly test your rules to ensure they are working as expected and protecting against the intended threats.
- Use the AWS WAF API: The AWS WAF API allows you to automate the creation, deployment, and management of WAF rules and configurations.
- Enable AWS Shield Advanced: AWS Shield Advanced provides additional protection against DDoS attacks and includes 24/7 support from AWS security experts.
- Implement the principle of least privilege: Ensure that you only grant access to your AWS WAF resources to those who require it and only to the necessary actions.
- Use multiple layers of security: Don’t rely solely on WAF for your application’s security. Instead, use a combination of security measures, including access control, encryption, and intrusion detection.
- Regularly review logs and metrics: Analyze your logs and metrics to identify patterns and unusual activity, as this can help you detect potential attacks before they cause any harm.
- Implement a disaster recovery plan: In the event of a breach, having a well-defined disaster recovery plan can help you minimize the impact of the breach and reduce downtime.
- Test your disaster recovery plan: Regularly test your disaster recovery plan to ensure that it works as intended and can effectively restore your systems and applications in the event of a breach.
- Integrate with other AWS services: AWS WAF can be integrated with other AWS services, such as AWS Lambda and Amazon CloudWatch, to create a more robust security solution.
- Stay up-to-date with the latest security best practices: Keep up-to-date with the latest security trends, threats, and best practices, as this can help you improve your security posture and protect your web applications more effectively.
By following these best practices, you can help ensure that your AWS WAF provides the best possible protection for your web applications and that your organization remains secure against the latest threats.
Overall, it’s important to regularly review and update your WAF configurations to ensure that they continue to provide effective protection against the latest threats. By following these best practices, you can help ensure the security and performance of your web applications.
Use cases for AWS WAF:
- AWS WAF is a powerful tool that can provide protection for web applications against a variety of cyber threats and attacks. Below are some typical scenarios in which AWS WAF can be employed:
- Protecting against common web attacks: AWS WAF can shield web applications against well-known web attacks, including SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF).
- DDoS mitigation: AWS WAF can provide defense against DDoS attacks by enabling users to establish rate-based rules that restrict the number of requests that can be made during a specific time period.
- Protection of APIs: AWS WAF can safeguard APIs from attacks, such as parameter tampering and content injection.
- Protection of content management systems: AWS WAF can provide security for CMS, like WordPress, Drupal, and Joomla, against recognized vulnerabilities and exploits.
- Geographical restrictions: AWS WAF can enforce geographical limitations on access to web applications, hindering attacks from specific regions or countries.
- Protection of e-commerce sites: AWS WAF can help protect e-commerce sites against fraudulent transactions, credit card skimming, and other attacks targeting sensitive user information.
- Protection of web applications on AWS: AWS WAF can secure web applications running on AWS, including those using Amazon API Gateway or Amazon CloudFront.
In summary, AWS WAF is a versatile solution that can safeguard web applications of various sizes and types against a wide range of cyber threats and attacks.
Competitors and Alternatives to AWS WAF
- FortiWeb Web Application Firewall.
- Cloudflare WAF.
- App & API Protector.
- F5 BIG-IP Advanced Web Application Firewall.
- Azure Web Application Firewall.
- Wallarm End-to-End API Security.
- The ThreatX Platform.
- Polaris WAAP.
Conclusion:
In conclusion, a Web Application Firewall (WAF) is an essential security tool for protecting web applications from a wide range of attacks, such as SQL injection, cross-site scripting (XSS), and more. A WAF is typically deployed between the web server and the internet and acts as a filter for incoming traffic, blocking malicious requests and allowing legitimate traffic to pass through.
A WAF can offer a range of pre-configured rules to help protect against common attacks, as well as the ability to create custom rules that can be tailored to specific applications. It can also provide additional layers of protection, such as rate limiting, geolocation blocking, and SSL/TLS termination.
However, it is important to note that a WAF is not a silver bullet and should not be relied upon as the sole means of securing a web application. It should be used as part of a comprehensive security strategy that includes other measures such as regular security audits, software updates, and employee training.
Overall, a WAF is a powerful security tool that can help protect web applications from a wide range of attacks, but it should be implemented and used with care and attention to best practices to ensure maximum effectiveness.







